In the digital age, data is the foundation of all corporations. This understanding is important for small business owners, e-commerce entrepreneurs and financial analysts who want to ensure that the data is secured and intact. One such mechanism is hash total. However, what on earth is a hash total and why it matters to your business? In this article I give an overview of hash totals, their importance in maintaining data integrity and how they are used in producing digital signatures.
What Is A Hash Total?
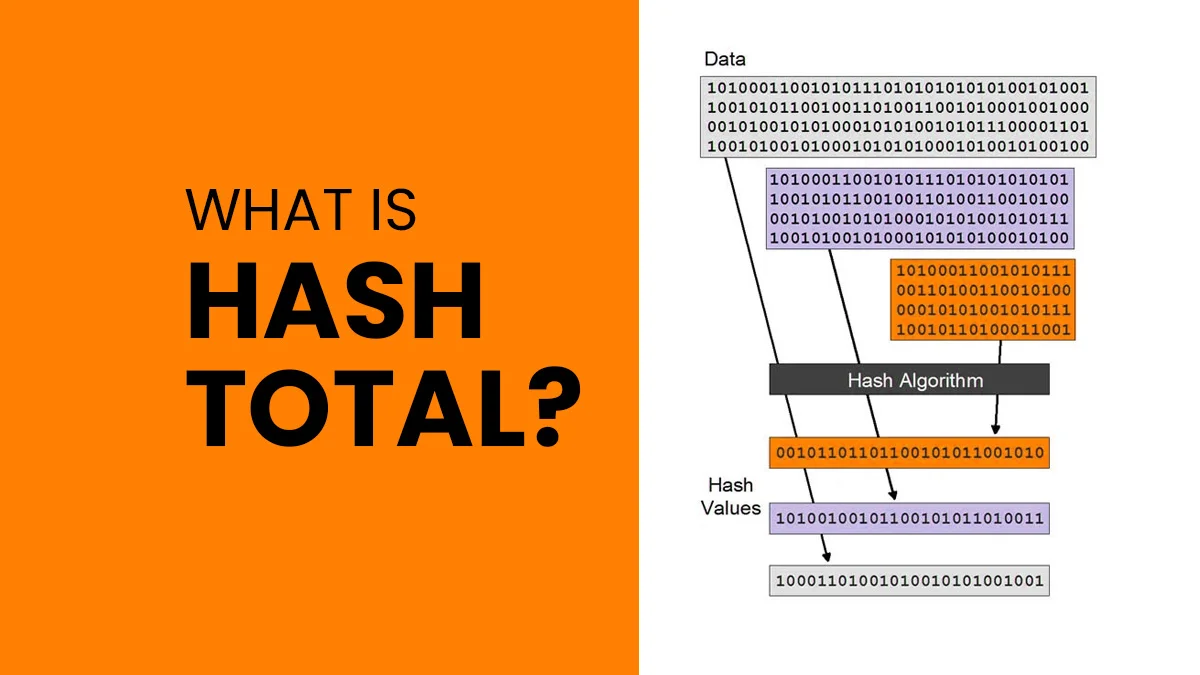
As far as computing and data management world goes, a hash total might sound like something from breakfast menu but it performs a vital function. To put it simply, this numeric value results from a string of text through a process known as hashing. For example, by taking a message (or input) apart and returning fixed-length string bytes which can be referred to as a digest that uniquely represents the data. Any tweaking in the data no matter how slight will always yield different has value. This feature makes hash totals invaluable when protecting and authenticating data integrity.
The Significance of Hash Totals in Data Integrity

Data integrity is critical for business operations, especially those that depend on digital transactions and records. Hash totals help maintain this vital aspect in this manner:
- Security: Hash totals guarantee the security of data by confirming that it has not been manipulated thus preventing information transmitted or stored from changing its original state.
- Efficiency: Checking the integrity of data through hash totals is faster than bit-by-bit comparison of data. It ensures that files have not been tampered with or corrupted, making it more efficient.
- Trust: The use of hash totals in digital transactions assures individuals involved that the data being exchanged is accurate and reliable hence developing trust among business operations.
A Multilayered Security Approach to Hash Totals and Digital Signatures
Digital security and data integrity are some other critical terms in the area of digital signatures. They combine hash totals with cryptography so that a signature is created that uniquely ties together both the document and its endorsing person. This process usually involves producing a message or document’s hash total, followed by encrypting this particular hash using an individual key. This recipient can then decrypt the sent message’s hash by using the sender’s public key, after which he can compare it with that generated from the received message. Matching of these hashes ensures that there was no change in messages and also confirms its source thereby validating its digital signature.
Using Hash Totals in your Business

For Small business owners, e-commerce entrepreneurs and financial analysts who want to implement or enhance their data integrity measures, having a clear understanding and use of hash totals is a move in the right direction. Here’s how to get started:
- Audit Your Data Handling Processes: Figure out which parts of your operations are critical for data integrity. This could include areas like money transfers, client information organization or sensitive company data.
- Choose Appropriate Tools and Protocols: Investigate hash functions and data integrity software that caters for the needs of your enterprise. Choose secure hashing algorithms with proven track record like SHA-256.
- Educate Your Team: Make sure that your employees comprehend what it means to maintain data integrity and know how to utilize the chosen tools and protocols.
- Regularly Assess Security Measures: Digital environments are always changing as well as ways by which data integrity can be compromised. Continually update security measures; frequently review them.
Conclusion
For companies involved in the digital ecosystem, the protection of data integrity is an absolute necessity. A hash total does not only apply to technology but also is a basic part of ensuring that data handling is secure and dependable. Using this in your operations means you are on the right path to protect the integrity of your business’ data. They play a critical role in maintaining data integrity through facilitating secure transactions, protecting customer’s information and verifying legitimacy of digital communications.
Hence in this world increasingly dependent on information, safeguarding that information is necessary for maintaining trust, reliability and success in one’s business pursuits.